...
| Info |
|---|
NOTE: If your supported solution is already cloud-based and/or is Internet-facing then it’s even easier to link the platform to your chosen scanning solution. Just follow the Connecting External Vulnerability Scanning Solutions guide to get started. |
Access Controls for
...
the Platform
For those scanning solutions that are only internal to your infrastructure and organisation (i.e. the scanners are not exposed to the Internet) you will need to allow access from the platform application platform through your Internet firewall(s) or via a Reverse Proxy. This is necessary so that the platform can establish an inbound connection to your scanning solution(s) and retrieve scan results.
...
The region in which your Platform is located will determine the public IP addresses of the Platform. Please refer to this article to check the region of your Platform
Please refer to this article for details of the Platform’s public IP addresses:
Source IP Addresses for Prism the Platform
Example Deployment - Platform access to Nessus via NAT/PAT Firewalls
Using Tenable’s Nessus Professional platform in the following example, if your organisation has deployed one or more ‘standalone’ Tenable Nessus Professional scanners across your internal network, and you are not using Tenable’s centralised scanner management platforms (e.g. Tenable.IO or Tenable.SC), each scanner must be exposed to the platform application via your primary Internet firewall(s) allowing the platform to retrieve scan results from each of the scanner’s API
...
| Info |
|---|
This example assumes the Tenable Nessus Professional Scanner is using the default management port of TCP-8834. If you are using alternative ports, please adjust firewall rules accordingly. |
Assume the following scenario:
An organisation has a single office network with a single Internet connection protected by a Firewall
The organisation’s platform tenant is within the UK Region
A Tenable Nessus Professional Scanner is deployed on the internal office network using a static private IP address of 192.168.100.1
The organisation has an available/spare public IP address of a.b.c.d and this will be used for the Tenable Nessus Professional Scanner
On the firewall, a NAT Rule and an Access Rule will be needed to permit access from Prismthe Platform:
A NAT Rule will be required to map the available public IP address of a.b.c.d to the scanner’s private IP address of 192.168.100.1
An Access Rule will be required to permit access from the platform to the public IP address mapped to the scanner (a.b.c.d) on TCP Port 8834
...
Using Tenable’s Nessus Professional platform in the following example, if your organisation has deployed one or more ‘standalone’ Tenable Nessus Professional scanners across your internal network, and you are not using Tenable’s centralised scanner management platforms (e.g. Tenable.IO or Tenable.SC), each scanner must be accessible to the platform application via an interim Reverse Proxy allowing the platform to retrieve scan results from each of the scanner’s API
...
| Info |
|---|
This example assumes the Tenable Nessus Professional Scanner is using the default management port of TCP-8834. If you are using alternative ports, please adjust the Reverse Proxy server-side rule accordingly. For the purpose of this example and in the context of Reverse Proxies, the Nessus Professional WebUI and API is considered the destination “Web Service” or “Web Application” Rootshell Security have successfully tested this deployment using nginx as a Reverse Proxy |
Assume the following scenario:
...
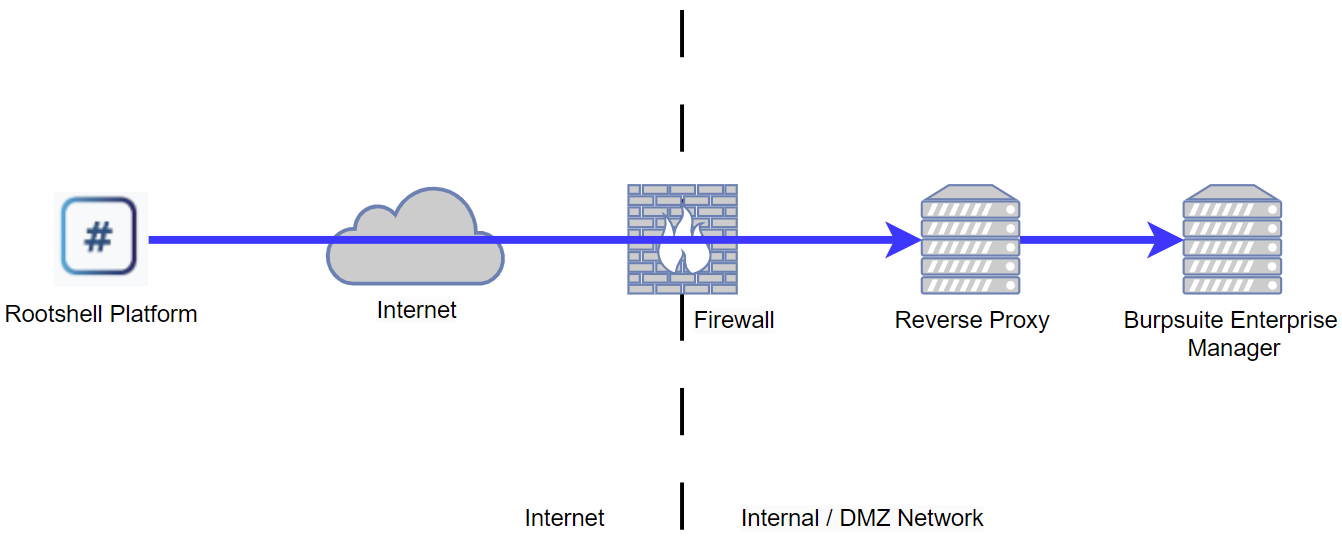
Example Deployment - Platform access to Burpsuite Enterprise via Reverse Proxies
...
| Info |
|---|
This example assumes the Burpsuite Enterprise Manager is using the default web management port of TCP-8080. If you are using alternative ports, please adjust your Reverse Proxy rules accordingly. For the purpose of this example and in the context of Reverse Proxies, the Burpsuite Enterprise WebUI and API is considered the destination “Web Service” or “Web Application” Rootshell Security have successfully tested this deployment using nginx as a Reverse Proxy |
...
| Note |
|---|
NOTE: Rapid7’s cloud-based Insight Platform is not currently supported by Prismthe Platform. Limitations in the Insight Platform API prevent the platform from retrieving results on a per-scan basis. |
...
| Info |
|---|
This example assumes the InsightVM Security Console is using the default management port of TCP-3780. If you are using alternative ports, please adjust firewall rules accordingly. |
...
Assume the following scenario:
An organisation has a single office network with a single Internet connection protected by a Firewall
The organisation’s platform tenant is within the UK Region
A InsightVM Security Console is deployed on the internal office network using a static private IP address of 192.168.100.1
The organisation has an available/spare public IP address of a.b.c.d and this will be used for the InsightVM Security Console
On the firewall, a NAT Rule and an Access Rule will be needed to permit access from Prismthe Platform:
A NAT Rule will be required to map the available public IP address of a.b.c.d to the InsightVM Security Console’s private IP address of 192.168.100.1
An Access Rule will be required to permit access from the platform to the public IP address mapped to the InsightVM Security Console (a.b.c.d) on TCP Port 3780
...
| Note |
|---|
NOTE: Rapid7’s cloud-based Insight Platform is not currently supported by Prismthe Platform. Limitations in the Insight Platform API prevent the platform from retrieving results on a per-scan basis. |
...
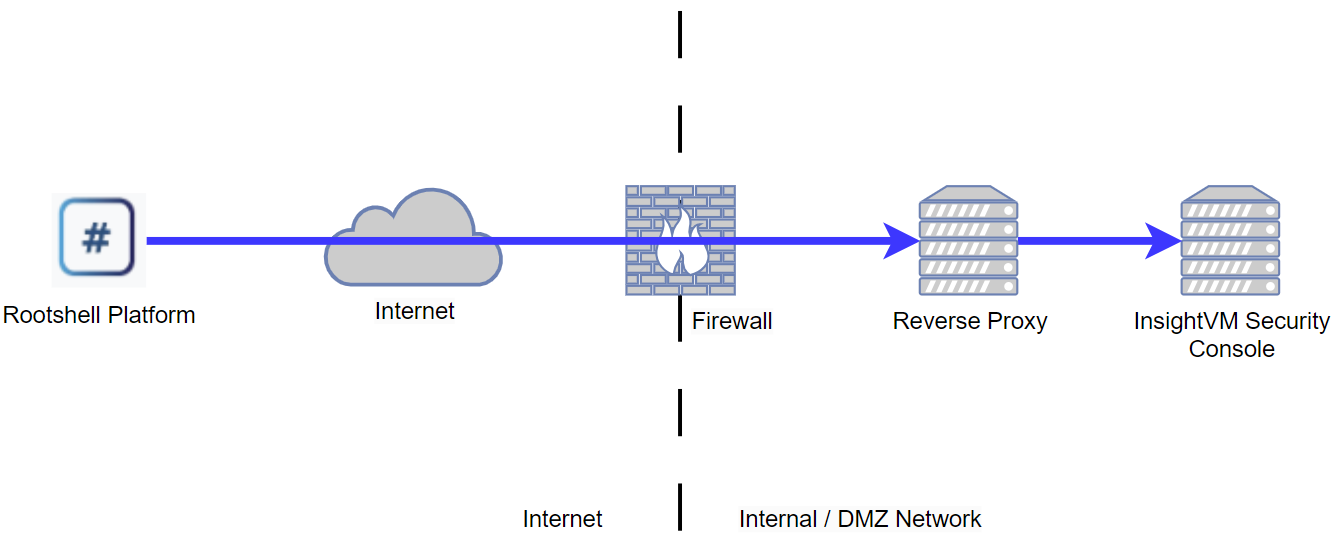
| Info |
|---|
This example assumes the InsightVM Security Console is using the default management port of TCP-3780. If you are using alternative ports, please adjust the Reverse Proxy server-side rule accordingly. For the purpose of this example and in the context of Reverse Proxies, the InsightVM Security Console WebUI and API is considered the destination “Web Service” or “Web Application” Rootshell Security have successfully tested this deployment using nginx as a Reverse Proxy |
...